G Data Endpoint Protection Business review
G Data CyberDefense AG is a German company, which has been around since 1985. Their main focus is on security software and in the past their scanners have incorporated features from both Avast and Bitdefender.
In recent years though G Data have introduced their own scan engine, which they incorporate into a number of their security products. G Data claims their Endpoint Protection Business (hereafter referred to as 'EPP Business') offers 'security for all endpoints' and 'next generation product technologies'.
Certainly the German software security giant knows how to talk a good talk - but is G Data Endpoint Protection Business the best endpoint protection software out there? Read on.
G Data Endpoint Protection Business: Plans and pricing
If you're looking for a broad brush overview of pricing for G Data Endpoint Protection Business, you'll be disappointed. The main product page does have link to request a quote. You can also request a consultation with one of G Data's experts.
In fairness G Data are by no means the only developer for endpoint security solutions that do this but a basic pricing model is always helpful when deciding if a product is right for your organization.
On the plus side, G Data does make it very easy to test out their software. Interested parties need only fill in an online form on their 'test' page to receive a download link for a trial version of EPP Business, as well as a temporary username and password.
G Data Endpoint Protection Business: Features
The main listed features of G Data Endpoint Protection Business include central management (more on this later), as well as mobile device management, anti-spam, a dedicated firewall and policy management. G Data also offers optional add-ons for 'Mail Server & Proxy Security'.
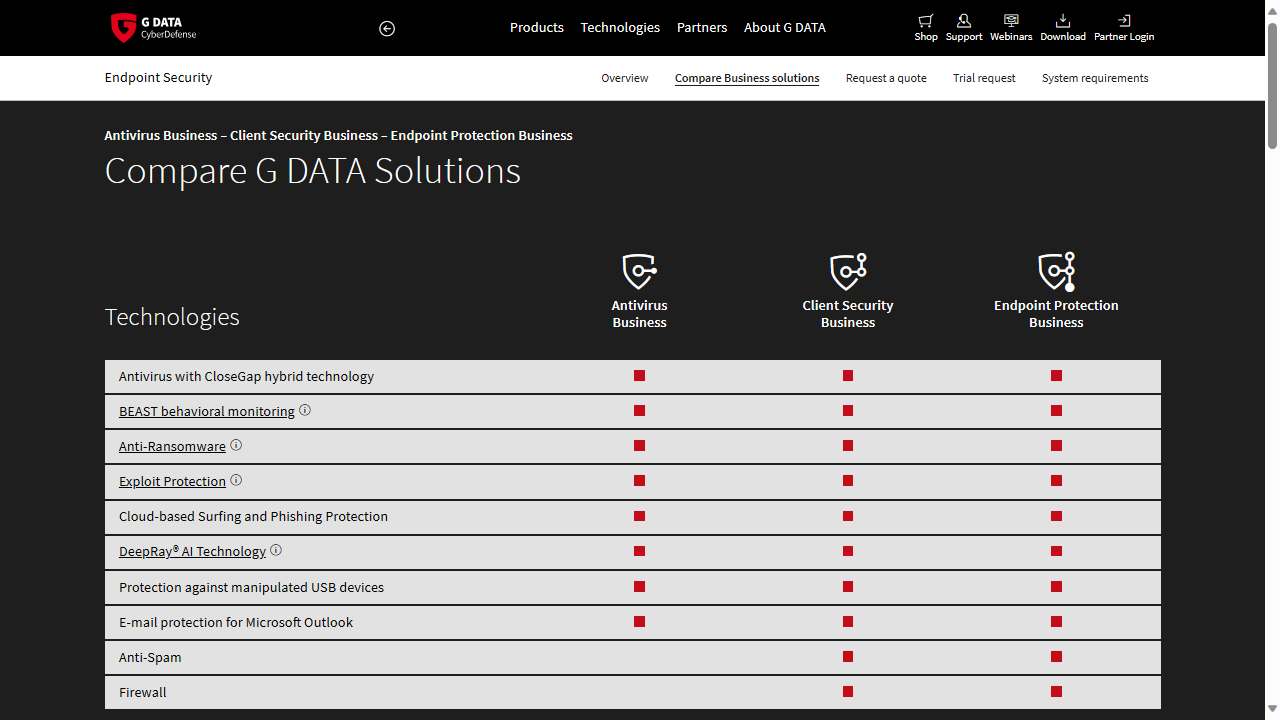
One point in the company's favor is that their product page actually provides a detailed comparison of G Data's various offering detailing what it offers above and beyond regular antivirus.
For instance, like G Data's Antivirus Business, Endpoint Protection Business includes the company's 'BEAST' behavioral monitoring, which supposedly records all system behavior in a graph to better detect malicious processes.
Both products also use G Data's 'DeepRay AI Technology', which the company claims is able to detect malicious files much faster than comparable technologies.
G Data also claims that Endpoint Protection Business Business also offers e-mail protection (Microsoft Outlook) only, anti-spam technology, protection against corrupted USB devices and a dedicated firewall.
G Data Endpoint Protection Business: Setup
We mentioned earlier that G Data make it very easy to fill in a contact form and receive a link to download a trial version of their product. Readers shouldn't take this for granted, as many endpoint security platforms either don't offer a free trial or demand payment information upfront.
However, in this case there's a catch. G Data Endpoint Protection Business isn't available as a cloud console, meaning you need to set up the installation to your own server.
On the downside this means you'll have to have the bandwidth and patience to download a 4.7GB compressed (ZIP) archive with the installation files, as well as a suitably provisioned server which can handle managing however many endpoints your organization has.
This could be an advantage though if your organization handles particularly sensitive data, as by setting up your own management servers you don't have to trust your endpoint information to a third party.
After starting the download, we went away for a cup of tea then decompressed the ZIP archive. The 'G Data Management Server' installer itself went like lightning but English-speaking users should have a care to make sure to choose their own language instead of the default (German).
The installer also prompts users to choose whether the target device will be the main server i.e. one which manages all network security clients or a secondary/subnet server. Next, users must choose the database installation method. For fewer than 1,000 clients the installer recommends using Microsoft SQL Server 2014 Express. You can also configure a connection to an existing database.
The installer will then begin copying files (including those for Microsoft SQL Server if selected) immediately. This took around 10 minutes in total on our test machine.
After the install is complete, the Management Server apps prompts for the login data sent in your registration e-mail. We were then asked to log in to the 'G Data Adminstrator' app. This is where we hit our first snag, as although we tried to use Windows login credentials the program refused to accept the password. It was only when we created a local administrator account on the computer that we were able to sign in.
When we were finally able to sign in, the 'G Data Administrator Setup Wizard' launched. In theory this allows network managers to install G Data's security client on endpoints. In practice we found it wouldn't accept our 'access' username and password. Luckily this isn't a major hurdle, as all the client installers for various versions of Windows were included in the original 4.7GB ZIP archive we downloaded earlier.
In order to install the client we had to input the management server name (be warned it's case sensitive), at which point we were prompted to restart the PC.
G Data Endpoint Protection Business: Interface
After restarting the PC we were surprised to see that G Data's Agent Software didn't automatically launch in the system tray. We fired up the Server Management program, only to see the client was shown as disconnected. We then found that the test machine's keyboard wasn't working.
This made it difficult for us to do any in-depth analysis of the software interface, so we decided to try again on a new, clean test machine running Windows 11.
On launching the installer again our test machine rebooted. We tried once more and this time the install completed the the G Data Security client icon appeared in the system tray. The G Data Management Server app however recorded it as not being connected at first. We were able to use the 'reset' function ultimately to get this working.
Once the client was installed, we did discover that there's no interface to speak of on the client side. The system tray icon contains a small menu for running updates and to provide more info 'About' the app itself.
The management interface however, was much more forthcoming. The main 'Dashboard' provides an easy to follow list of security events, accompanied by helpful infographics on client connections, warnings and the status of reports.
The 'overview' section at the bottom left of the main window also contains a list of launcher icons to main functions like 'Security' and 'Client Logs'.
When reviewing endpoint security platforms our first test is to attempt to download a fake computer virus provided by the good people of EICAR. Upon attempting to download the virus onto our test Windows 11 machine using Microsoft Edge in compressed (ZIP) format, we found we were unable to extract the file: G Data Security Client had detected the suspect file and changed its permissions so we couldn't interact with it.
We were only able to discover this by logging into the Management server and reviewing the security logs however. There was no pop up or alert on the client side, nor was the file quarantined.
Our next test was to copy a new, real computer virus which we'd caught in the wild into the test machine's "Downloads" folder. We do this to check if endpoint security software can detect files based on suspicious behavior, not just compare them to a database of known virus signatures.
We were disappointed to see that the file copied across without issue. When we tried to run it our test machine became infected with the virus. After checking the Management Server we could see no security alerts on that side, showing that the protection G Data offers has its limits. This is particularly worrying considering that the G Data client disables Windows Security's own real-time protection, which would probably have detected this virus.
G Data Endpoint Protection Business: Final verdict
The G Data programs we installed displayed a splash screen stating "Trust in German Sicherheit' (Security)". If users are expecting the stereotypical German organization and attention to detail with this product though, they may be disappointed. The setup process is convoluted, given it took us several tries to get it working on our test machines. The real-time detection of threats is also limited. We also would have appreciated a basic pricing model, to give interested parties some idea of how much a subscription will cost.
The only points we can really find in G Data's favor is that you have the option to install the management platform on your server, which has some security benefits. The registration process to obtain a download link to evaluate the software is also relatively painless compared to similar platforms.
Overall though, we feel that there are other endpoint security platforms that are easier to set up and which offer better protection.
0 comments:
Post a Comment