Steganos Safe
Many people think that encryption is a modern concept, but it’s as old as human communication. The first documented use is in non-standard hieroglyphs found on Egyptian artefacts dating from 1900 BC, clearly an attempt to stop everyone from reading their meaning.
Ancient scholars understood substitution cyphers and used them to send messages that only the intended recipient might read.
However, the turning point for cryptology came with advancements in mathematics available in the 19th century, leading to the military cyphers used in World War I and the mechanical encryption machines, like Enigma, widely used in World War II.
The complexity of these devices and the importance of using cryptanalysis to break these codes lead to the first programmable computers.
Today we’re looking at a powerful encryption tool designed to secure files inside an impenetrable bubble of mathematics that only a person with the correct password can access. Steganos Safe offers this functionality and more for a yearly fee. Let’s find out if it justifies that outgoing.
Price
Steganos Safe 22 is the latest release and costs $34.99 (£34.84) directly from Steganos. The downloadable software has a license for use on up to 5 PCs for a year. There are no longer-term licences or bulk purchasing reductions at the point of purchase, sadly.
What is offered is a 30-day fully-functional trial, allowing a potential customer to experience the software entirely.
Any encrypted Safe made using the software can still be read once the trial or licensing ends. They just can’t be added to or changed without a current license.
Features
Microsoft Windows 10 or 8
At least 1 GB RAM (32 & 64 bit)
100 MB hard disk space
An Internet connection
Version 22 of Steganos Safe was released on September 10th, 2020 and is the latest incarnation of a product that started life more than twenty years ago.
While only a couple of months old during this review, Steganos has already released seven updates to the original 22.0.0 release, and the version we used is 22.3.0 (Revision 12860).
These changes included bug fixes, interface optimizations and a few extra enhancements.
The functionality of Steganos Safe is basic but highly focused on delivering what the customers most need for protecting documents from prying eyes.
It has two components, the Safe creation and maintenance functionality and a file shredder for destroying documents irretrievably. Previously the Shredder was separate software technology, but with version 22, it is now integrated.
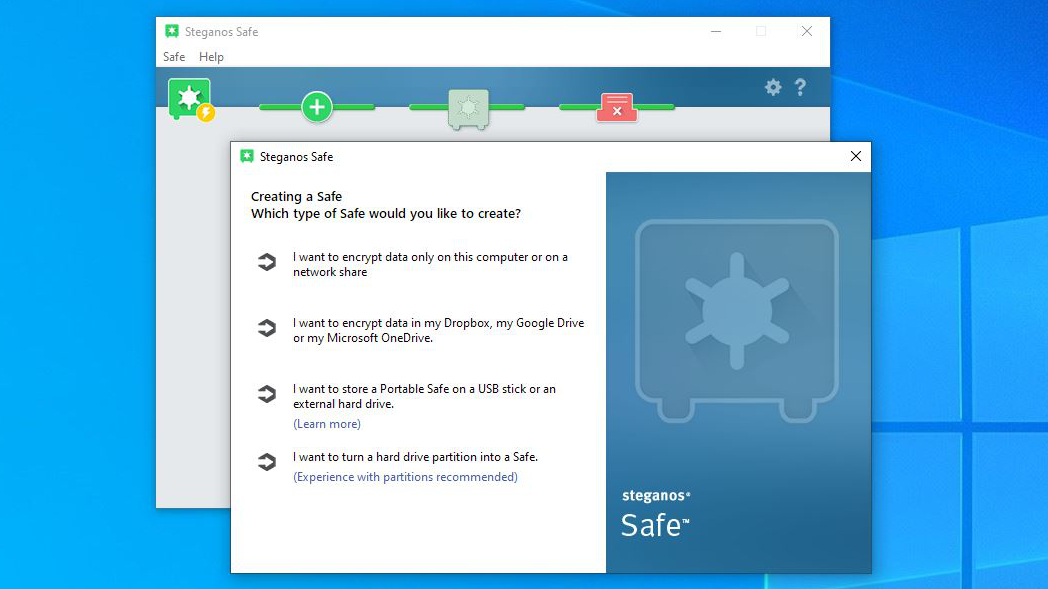
However, the core functionality is the encryption engine, and it can be used in many subtle ways to protect files and folders on the installation computer, entire partitions, network-attached folders, external hard drives, USB sticks, and even Cloud storage Dropbox, Microsoft OneDrive, MagentaCLOUD and Google Drive.
The scope of these possibilities goes a little way to negate the limitation that this software only works on Windows machines. Still, it would be preferable to see a mobile version for iOS and Android eventually.
Creating a safe, especially one that resides on the computer, is remarkably straightforward, and alongside the password mechanism that we’ll talk about more later, the safe file is hidden on the system to avoid it being an easy target for anyone searching the system.
Hiding the file is something we’ve seen other systems do, but the caveat with that stealth approach is that backup applications might not include the invisible file when securing drive contents.
The workaround that Steganos devised for small safes under 3GB was to make the Safe appear to be a standard document, like a video or audio file. The system even allows you to pick an existing MP3, M4A, AVI, WMV or EXE file and embed the safe inside it.
That file will still work like it should on the system, playing video or music, even when it’s been modified.
We like that thinking because the container can be backed up and doesn’t scream ‘secure data here’ to anyone that’s invaded the system.
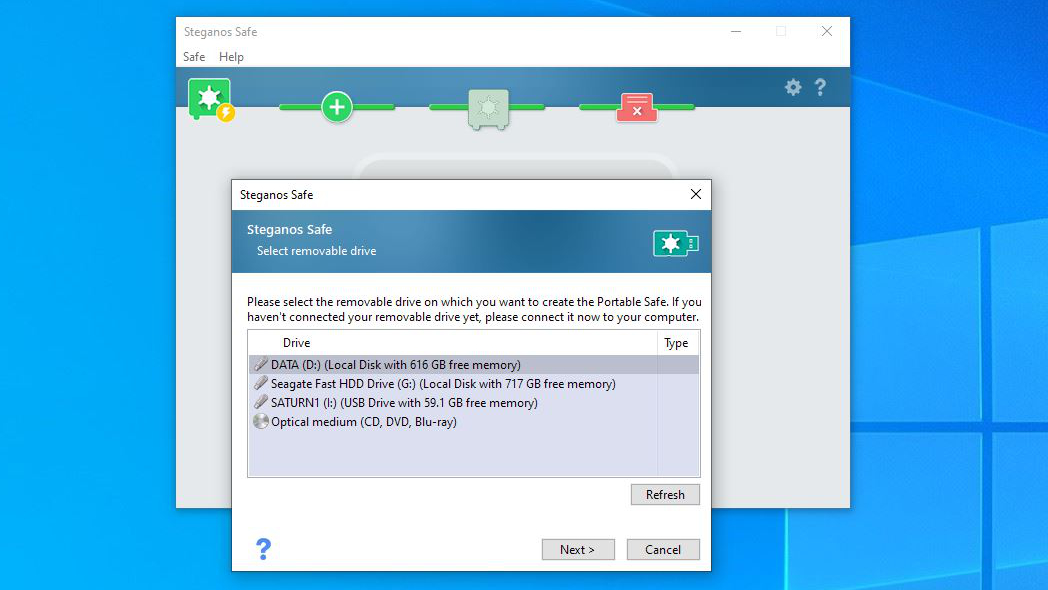
The working space of a safe is limited to 2TB, but the Safe size can scale from a much smaller original size dynamically. USB portable safes are size constrained by the file format used on the drive, but they work the same way in most respects as the local safes.
The encryption of Cloud storage is another option that makes sure that anyone seeing the files stored there has both Steganos Safe on their system and the right credentials to gain access.
Of all the functionality, the one feature that could be potentially dangerous to unfocused users is the ability to encrypt a partition.
What’s different about this option is that when you select the partition to encrypt, you are given an unambiguous warning that it will erase the existing contents of that partition.
For those that use a computer while thinking about something else entirely, this could easily go wrong. Still, you need to launch Steganos Safe with administrator privileges to make these changes, hopefully avoiding the disastrous reflex clicker.
This feature is best configured when the PC is being initially prepared, as partition sizes can be more easily adjusted, and allocating a special partition for this purpose is relatively painless for experienced users.
Encrypting partitions might require more knowledge than the other options, but the end result is a simple to use solution where the PC has a specific drive that is locked from access to those without the password. But the security side of this solution is more complicated than just a password, and we’d consider it one of the strengths of this offering.
Security
Steganos takes security very seriously since some of the tricks employed in Steganos Safe are more sophisticated than we’ve seen from competitor solutions.
As with any system that uses passwords, how good those passwords are is critical to securing or potentially undermining that.
That said, it is possible to define highly insecure passwords, though the software will tell you that they’re poor and not try to convince you they’re fine when they’re not.
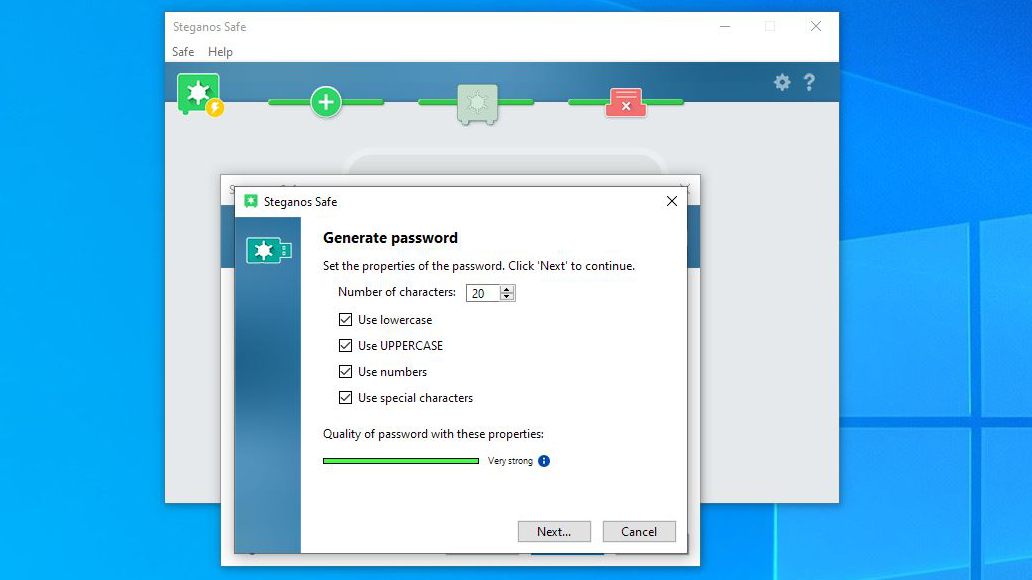
The maximum password length is 20 characters, and you are encouraged to use upper, lower, special characters for maximum impact. The system will autogenerate passwords or make them up from picture selections should you want the least predictable passwords.
Once a password is generated, it is copied to the clipboard to put into a password repository if you use one of those.
For manually input passwords, a virtual screen keyboard is provided, avoiding the possibility of a reveal to any keylogging software installed on the system.
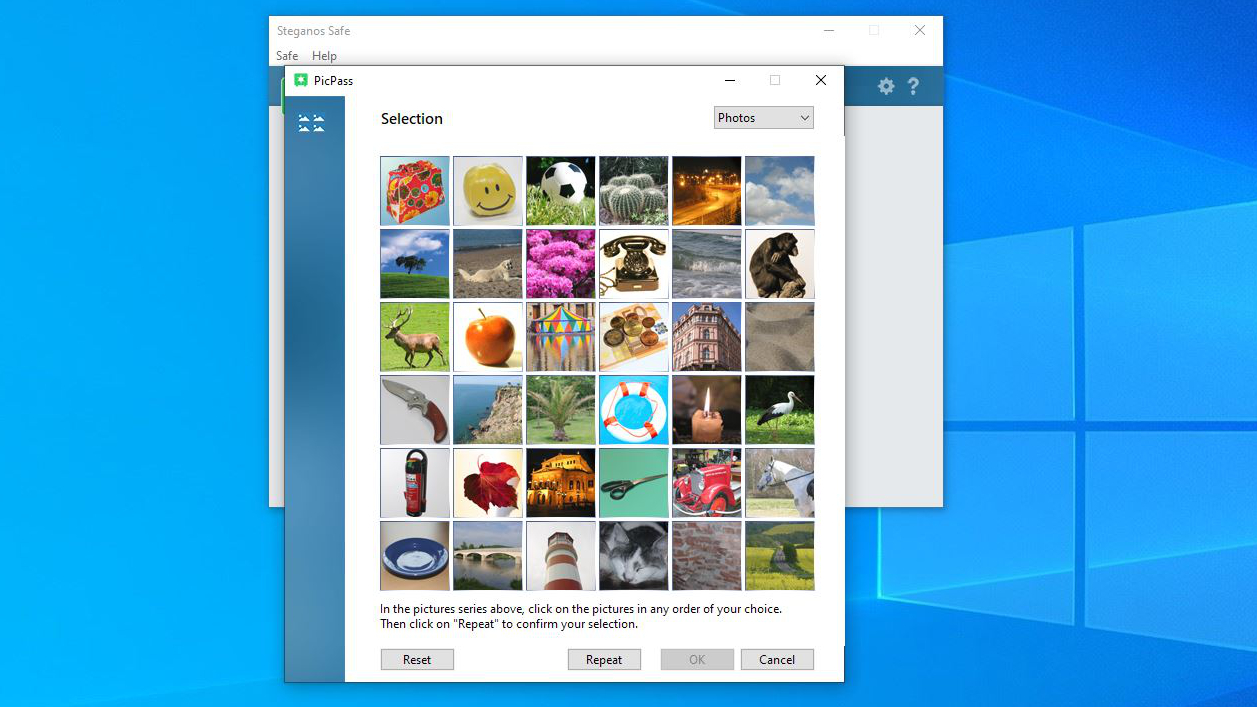
If passwords aren’t enough, two-factor authentication is available with a QD pattern to enable the safe to appear on Google Authenticator or simple services on other platforms.
Our only reservation about this 2FA implementation is that instead of creating a single 2FA link for this Steganos Safe user account, it makes an entirely new one for each safe you create. Each of these links has a specific Safe name, but having so many on the Authenticator list could quickly become tiresome.
Alongside the password and 2FA options, an additional emergency password can be defined to provide a read-only entry to the encrypted Safe for others to use. Again, this is Safe specific and not a global backdoor.
The use of 384-Bit AES-XEX encryption realistically scuppers any practical brute-force hacking approach to unlocking a Safe. That leaves the only weaknesses being hacking that can display what is happening on screen or the copying of passwords to insecure locations or their appearance in documents or emails.
No encrypted system is 100% secure, but this one should protect files from opportunity hackers at the very least.
In use
As encryption tools go, this one is simplicity personified.
Each option provides a wizard that guides the user through creating a secure space for sensitive files and explaining any nuances to the feature they’re using.
As an example, when a portable safe is created, the file size limitations of a FAT32 file system are explained, and along with the standard password, you are also encouraged to create an Emergency password that allows read-only access to others should they need that.
What is also good about all the solutions is that the level of security you wish to use is highly granular, enabling it to be simple for less critical data and then much stronger for genuinely sensitive files.
Forcing all users to use complex 20-character passwords would probably end badly for many of them, so having some flexibility about how secure a Safe can be is appropriate.
However, surprisingly we did find a few wrinkles in this system given the number of updates that it has seen. The wizard for creating portable partitions is entirely unaware of network drive letters and will place its virtual safe driver over them if you insist, annoyingly.
You can specify drive letters to avoid this, but surely it should only use drive letters not already in use?
Another curiosity is that when a portable Safe is created, it places the files needed to provide local access to the contents on the same drive. Using the cut-down USB version of Safe doesn’t use up a license, but it must be installed on a remote system for access. And that system might need to reboot once the Steganos encryption engine has been installed locally.
A solution that didn’t install files on other computers would be preferable, but that’s a limitation of how Steganos Safe operates at this time.
We’ve also previously mentioned the 2FA idiosyncrasies, another aspect that needs adjustment.
Overall, this is a solid solution that works well in many situations. Considering the number of updates we’ve seen issued, if a significant issue exists, it is likely to be fixed quickly.
Final verdict
It’s interesting to compare this product with others that we recently covered, and Steganos Safe is undoubtedly superior in several important ways.
Its encryption technology is excellent using a 384-bit model, its password restrictions can be strong, and probably most importantly, it offers two-factor authentication so that even if the password can be guessed or revealed, the safe is protected.
For some, they might find the need for complex passwords and using their mobile device for the second level of protection too much trouble. But, it’s realistically the difference between something that looks secure and a solution that under most circumstances will be.
Where Steganos also wins out is in respect of the licensing, since a single yearly payment gives access to the tool on five computers for a whole year. And, if you choose not to pay for another year, protected contents can still be accessed, even if they can’t be updated.
Its biggest issue is the lack of a mobile version or support for any other OS than Windows. While Windows is still important to many, years from now, that may no longer be the case and support for Linux, and by definition, Android could become critical.
We’d also like to see a means to bundle a simple decryption tool on USB sticks allowing files to be unlocked without installing files on a remote system.
Hopefully, version 23 or 24 will come along with some of those enhancements. But even without those features, this is an effective and well-designed tool that provides precisely the functionality that many users need to protect sensitive documents.
0 comments:
Post a Comment