Inky
Inky was founded in 2008 as a platform to provide secure email for enterprises. It started under a different name, Arcode, before rebranding a few years later.
This platform incorporates artificial intelligence to detect and block suspicious email activities like forgery and spear-phishing attempts. It plugs into existing email systems like Microsoft Exchange, Microsoft 365, and Google Workspace to analyze emails and alert users if it detects any anomalies.
Inky, the company, is based in Maryland, USA.
Inky: Plans and pricing
Unlike most email tools, Inky doesn’t have a standard pricing structure. You have to contact the company’s sales team and arrange a custom plan depending on the size of your enterprise. This flexible pricing structure should be a hint that the platform is pretty expensive.
Inky: Features
Phishing is the primary cause of data leaks in enterprises. To the unaware, it refers to criminals impersonating an organization via email or any other means of communication to steal data.
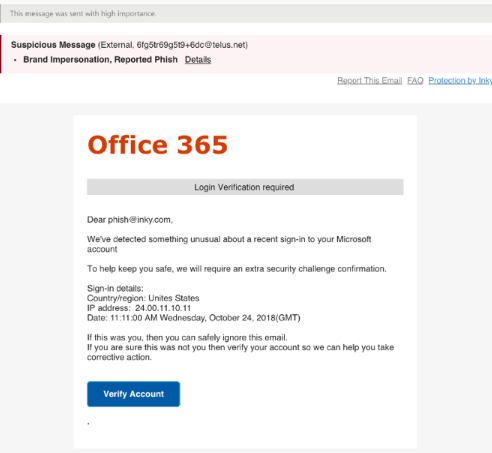
To tackle phishing, Inky analyzes any inbound email and signals any suspicious behavior it detects with interactive banners that guide the users to take adequate actions. It doesn't only detect phishing attempts but also turns them into teaching sessions to prevent users from falling victim to a similar attempt in the future.
If you integrate Inky with your email client, every inbound email will have a grey banner (indicating nothing suspicious), a yellow banner (proceed with caution), or a red banner (danger). These banners let you know what to click and what not to click to lessen your chances of falling victim to phishing attempts.
If you see a red banner, you'll also see a link that says "Details". Click this link, and the Inky email assistant will show you what exactly is wrong with the flagged email. It's an effective way of educating users on real-world threats in their email inboxes.
When you encounter a flagged inbound email, you can click the "Report This Email" link to let your company's IT department investigate further.
One of the most common phishing activities involves impersonating a service provider and a bank’s identity to send forged invoices and trick companies into paying them. Luckily, Inky has a tool to tackle this problem. It uses natural language processing (NLP) algorithms to identify emails that are likely forged and draws your attention to them.
Outbound emails need protection as much as inbound ones. Employees send many emails daily, and they can intentionally or unintentionally include sensitive information within them. To avoid this, Inky scans every outgoing email for sensitive content. If it detects any, it flags it for approval by a chosen administrator or manager.
IT admins can create custom rules from their Inky dashboard to define how Outbound Mail Protection will work for their teams. For example, you can set Inky to flag an email for approval if it detects any suspicious link within it. You can also add a mandatory requirement to encrypt outgoing emails.
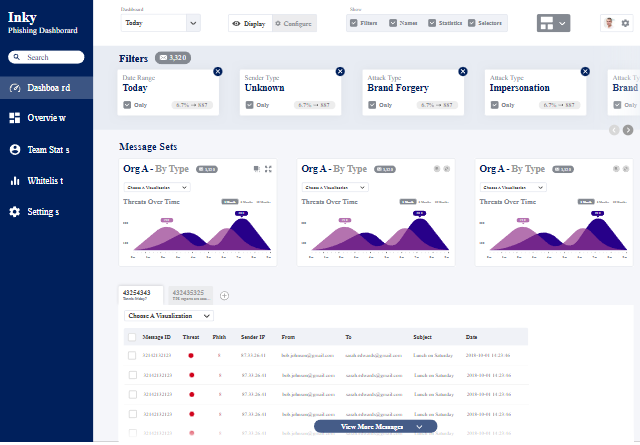
Inky uses a mix of detection tools to identify sensitive data within emails. It cross-references multiple data points such as keywords and specific figures and uses pattern matching to discover sensitive information, e.g., credit card information and bank routing numbers. It’s not perfect and may occasionally flag valid emails, but it offers solid protection compared to using an email provider’s default security tool.
Though Inky tries as much as possible to detect phishing attempts, it's not absolutely perfect and neither are humans within an organization. Some email accounts may get compromised in the end but Inky still has tools to tackle threats coming from within.
This platform builds behavior models of email senders within your organization using specific information like the display name, location, device type, and email client. If an email suddenly doesn't match the model of a sender, Inky can flag it as a suspected impersonation attempt requiring a manual review.
The fast alerts give your IT department the opportunity to eliminate any account it deems compromised and prevent a potential cyber catastrophe.
A common vector through which attackers break into a corporate network is by attaching malicious documents to an email. If the targeted email recipient opens the attachment, they can unknowingly install malware capable of destroying or stealing data.
Inky scans through every email attachment to detect malware and alert the recipient. The company claims a 99.7% accuracy for its analysis tool.
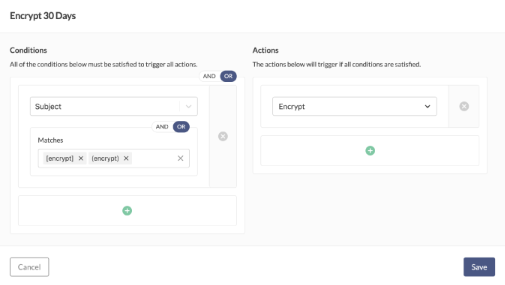
You can encrypt all outgoing emails to keep data secure within your corporate network. Inky uses 256-bit encryption to protect emails. Just add the word [encrypt] to the subject line of an email and it's good to go. The recipient will receive an email notification about the encrypted message, which they can view with Microsoft or Google credentials or by requesting a “magic link” from the sender.
Inky: Interface and use
Inky isn’t an email client of its own but connects to three corporate email providers – Microsoft Exchange, Microsoft 365, and Google Workspace. But, it has a dashboard that IT admins or managers can use to customize email settings for employees. According to customer reviews, navigating the dashboard can be pretty difficult but not overly so.
Inky: Support
Inky’s official website has a lot of free resources that teach enterprises how to avoid email-based attacks. For customers, it offers direct telephone support 24/7, which is expected given the platform’s price range.
Inky: The competition
Well-known alternatives to Inky include Darktrace, Cisco Secure Email, and the Proofpoint Email Protection Suite. These three platforms offer even more sophisticated features than Inky but can be more expensive.
Inky: Final verdict
Cyber attacks are increasing rapidly and it’s compulsory for enterprises to be on their guard. Inky provides adequate tools to ensure that your enterprise doesn’t get compromised through phishing attempts and all other types of email-based attacks. It does its job well but the price range is out of reach for small enterprises.
0 comments:
Post a Comment